A security analyst needs to prioritize vulnerabilities for patching. Given the following vulnerability and system information:
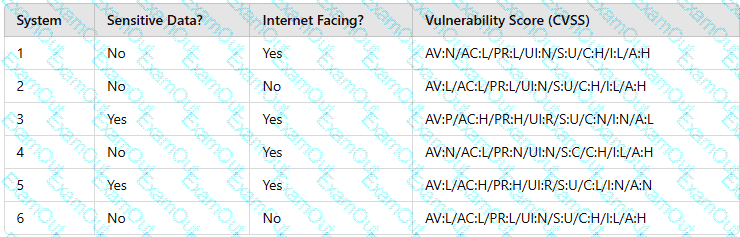
Which of the following systems should the analyst patch first?
An analyst is trying to capture anomalous traffic from a compromised host. Which of the following are the best tools for achieving this objective? (Select two).
A Chief Information Security Officer has requested a dashboard to share critical vulnerability management goals with company leadership.
Which of the following would be the best to include in the dashboard?
During a tabletop exercise, engineers discovered that an ICS could not be updated due to hardware versioning incompatibility. Which of the following is the most likely cause of this issue?
Which of following would best mitigate the effects of a new ransomware attack that was not properly stopped by the company antivirus?
A technician identifies a vulnerability on a server and applies a software patch. Which of the following should be the next step in the remediation process?
An analyst reviews the following web server log entries:
%2E%2E/%2E%2E/%2ES2E/%2E%2E/%2E%2E/%2E%2E/etc/passwd
No attacks or malicious attempts have been discovered. Which of the following most likely describes what took place?
A security analyst scans a host and generates the following output:
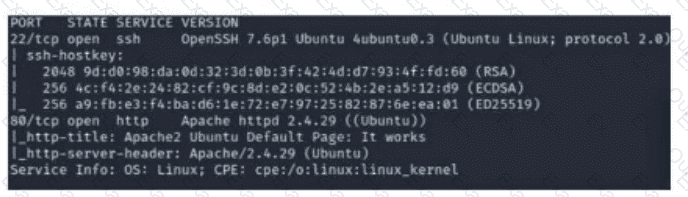
Which of the following best describes the output?
A zero-day command injection vulnerability was published. A security administrator is analyzing the following logs for evidence of adversaries attempting to exploit the vulnerability:
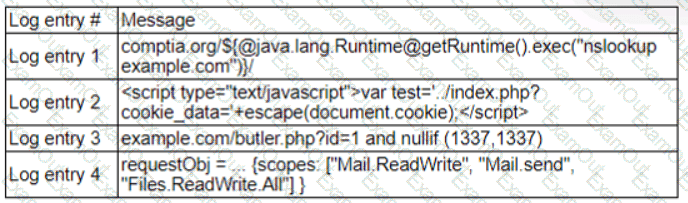
Which of the following log entries provides evidence of the attempted exploit?

