During the development process, the team identifies major components that need to be rewritten. As a result, the company hires a security consultant to help address major process issues. Which of the following should the consultant recommend tobestprevent these issues from reoccurring in the future?
A security team is concerned with attacks that are taking advantage of return-oriented programming against the company's public-facing applications. Which of the following should the company implement on the public-facing servers?
A compliance officer is responsible for selecting the right governance framework to protect individuals' data. Which of the following is the appropriate framework for the company to consult when collecting international user data for the purpose of processing credit cards?
A technology company developed an in-house chat application that is used only by developers. An open-source library within the application has been deprecated. The facts below are provided:
The cost of replacing this system is nominal.
The system provides no revenue to the business.
The system is not a critical part of the business.
Which of the following is the best risk mitigation strategy?
A software development company needs to mitigate third-party risks to its software supply chain. Which of the following techniques should the company use in the development environment to best meet this objective?
A company has a website with a huge database. The company wants to ensure that a DR site could be brought online quickly in the event of a failover. and end users would miss no more than 30 minutes of data. Which of the following should the company do to meet these objectives?
Users from the marketing department (192.168.0.1/24) are reporting performance issues with an on-premises application server (192.168.0.9). The application server should only be accessed internally. A security analyst reviews various logs and finds the following information:
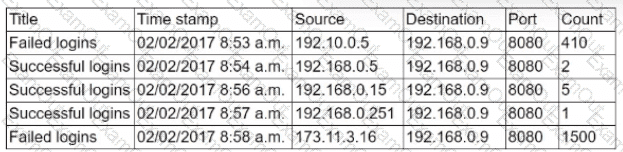
Which of the following should the security analyst perform next to improve performance and ensure the application server is secured as required?
A company with multiple locations has taken a cloud-only approach to its infrastructure The company does not have standard vendors or systems resulting in a mix of various solutions put in place by each location The Chief Information Security Officer wants to ensure that the internal security team has visibility into all platforms Which of the following best meets this objective?
A security engineer investigates an incident and determines that a rogue device is on the network. Further investigation finds that an employee's personal device has been set up to access company resources and does not comply with standard security controls. Which of the following should the security engineer recommend to reduce the risk of future reoccurrence?
The primary advantage of an organization creating and maintaining a vendor risk registry is to:
A security engineer is trying to identify instances of a vulnerability in an internally developed line of business software. The software is hosted at the company's internal data center. Although a standard vulnerability definition does not exist, the identification and remediation results should be tracked in the company's vulnerability management system. Which of the following should the engineer use to identify this vulnerability?
A company performs an annual attack surface analysis and identifies a large number of unexpected, external-facing systems. The Chief Information Security Officer (CISO) wishes to ensure this issue does not reoccur. Which of the following should the company do?
An internal security audit determines that Telnet is currently being used within the environment to manage network switches. Which of the following tools should be utilized to identify credentials in plaintext that are used to log in to these devices?
A cyberanalyst for a government agency is concerned about how Pll is protected A supervisor indicates that a Privacy Impact Assessment must be done. Which of the following describes a function of a Privacy Impact Assessment?
A security administrator at a global organization wants to update password complexity rules for a system containing personally identifiable information. Which of the following would be the best resource for this information?

