A security analyst discovered that the company's WAF was not properly configured. The main web server was breached, and the following payload was found in one of the malicious requests:
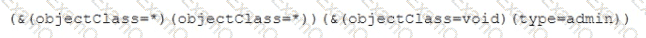
Which of the following would BEST mitigate this vulnerability?
The OS on several servers crashed around the same time for an unknown reason. The servers were restored to working condition, and all file integrity was verified. Which of the following should the incident response team perform to understand the crash and prevent it in the future?
A company is migrating its data center to the cloud. Some hosts had been previously isolated, but a risk assessment convinced the engineering team to reintegrate the systems. Because the systems were isolated, the risk associated with vulnerabilities was low. Which of the following should the security team recommend be performed before migrating these servers to the cloud?
During a recent breach, an attacker was able to get a user's login credentials by cracking a password that was retrieved via a stolen laptop. The attacker accessed the hashed passwords from the hard drive when it was connected to another device. Which of the following security measures could have helped prevent this account from being compromised?
An organization developed a containerized application. The organization wants to run the application in the cloud and automatically scale it based on demand. The security operations team would like to use container orchestration but does not want to assume patching responsibilities. Which of the following service models best meets these requirements?
An internal security assessor identified large gaps in a company's IT asset inventory system during a monthly asset review. The assessor is aware of an external audit that is underway. In an effort to avoid external findings, the assessor chooses not to report the gaps in the inventory system. Which of the following legal considerations is the assessor directly violating?
A security administrator wants to enable a feature that would prevent a compromised encryption key from being used to decrypt all the VPN traffic. Which of the following should the security administrator use?
Which of the following best describes what happens if chain of custody is broken?
An administrator completed remediation for all the findings of a penetration test and notifies the management team that the systems are ready to be placed back into production. Which of the following steps should the management team require the analyst to perform immediately before placing the systems back into production?
To save on device life-cycle costs, a company is transitioning to a BYOD deployment scheme for enterprise mobility. Local laws protect users from corporate-initiated wiping or manipulation of data not owned by the company. Which of the following techniques would best protect corporate data while ensuring the integrity of private data?
When managing and mitigating SaaS cloud vendor risk, which of the following responsibilities belongs to the client?
A DNS forward lookup zone named complia.org must:
• Ensure the DNS is protected from on-path attacks.
• Ensure zone transfers use mutual authentication and are authenticated and negotiated.
Which of the following should the security architect configure to meet these requirements? (Select two).
An organization has an operational requirement with a specific equipment vendor The organization is located in the United States, but the vendor is located in another region Which of the following risks would be most concerning to the organization in the event of equipment failure?
A security architect is improving a healthcare organization's security posture. Most of the software is cloud-based, but some old applications are still running on a server on-site. Medical devices using such applications require very low latency. The most important consideration isconfidentiality, followed byavailability, and thenintegrity. Which of the following is thefirst stepthe security architect should implement to protect PII?
A company has retained the services of a consultant to perform a security assessment. As part of the assessment the consultant recommends engaging with others in the industry to collaborate in regards to emerging attacks Which of the following would best enable this activity?

