Scenario: A Citrix Architect needs to plan for a customer environment in which more than 10,000 users will need access. The networking infrastructure needs to be able to handle the expected usage.
Which business driver should be prioritized based on the customer’s requirement?
Scenario: A Citrix Architect needs to assess an existing NetScaler configuration. The customer recently found that members of certain administrator groups were receiving permissions on the production NetScaler appliances that do NOT align with the designed security requirements.
Click the Exhibit button to view the configured command policies for the production NetScaler deployment.
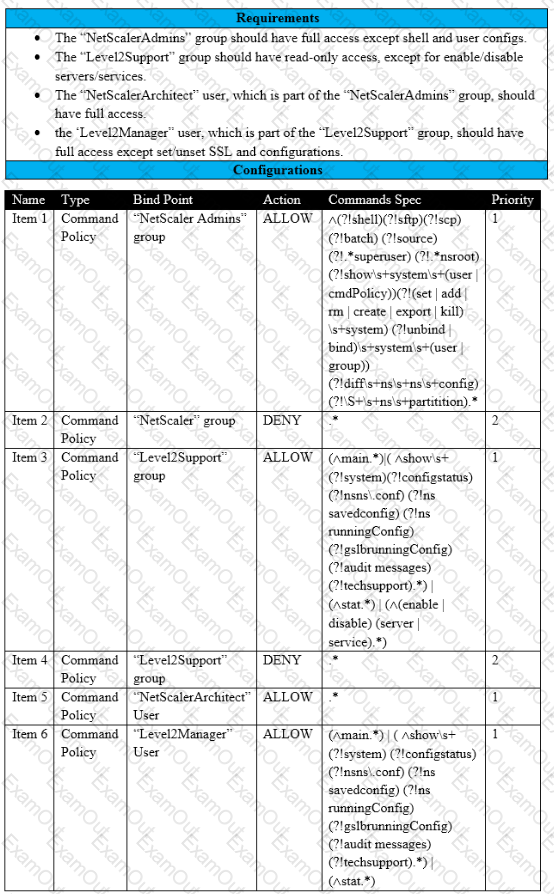
To align the command policy configuration with the security requirements of the organization, the _______ for ______should change. (Choose the correct option to complete the sentence.)
Scenario: A Citrix Architect has deployed two MPX devices, 12.0.53.13 nc and MPX 11500 models, in a high availability (HA) pair for the Workspace labs team. The deployment method is two-arm. and the devices are installed behind a CISCO ASA 5585 firewall. The architect enables the following features on the Citrix ADC devices: Content Switching. SSL Offloading, Load Balancing, Citrix Gateway, Application Firewall in hybrid security, and Appflow. All are enabled to send monitoring information to Citrix Application Delivery Management 12.0.53.13 nc build. The architect is preparing to configure load balancing for Microsoft Exchange 2016 server.
The following requirements were discussed during the implementation:
All traffic needs to be segregated based on applications, and the fewest number of IP addresses should be utilized during the configuration.
All traffic should be secured, and any traffic coming into HTTP should be redirected to HTTPS.
Single Sign-on should be created for Microsoft Outlook web access (OWA).
Citrix ADC should recognize Uniform Resource Identifier (URI) and close the session to Citrix ADC, when users hit the Logoff button in Microsoft Outlook web access.
Users should be able to authenticate using user principal name (UPN).
The Layer 7 monitor should be configured to monitor the Microsoft Outlook web access servers, and the monitor probes must be sent on SSL.
Which Responder policy can be utilized to redirect the users from http://mail.citrix.com to https://mail.citrix.com/owa ?
Scenario: A Citrix Architect has deployed an authentication setup for the load balancing virtual server for the SAP application. The authentication is being performed using RADIUS and LDAP. RADIUS is the first factor, and LDAP is the second factor in the authentication. The Single Sign-on with SAP application should be performed using LDAP credentials. Which session profile should be used to perform the Single Sign-on?
Scenario: A Citrix Architect needs to deploy a NetScaler appliance for Workspacelab, which will provide application load balancing services to Partnerlab and Vendorlab.
The setup requirements are as follows:
A pair of NetScaler MPX appliances will be deployed in the DMZ network.
High availability will be accessible on the NetScaler MPX in the DMZ Network.
Load balancing should be performed for the mail servers for Partnerlab and Vendorlab.
The traffic for both of the organizations must be isolated.
Separate Management accounts must be available for each client.
The load-balancing IP addresses must be identical.
A separate VLAN must be utilized for communication for each client.
Which solution can the architect utilize to meet the requirements?
Which two NetScaler cookies indicate the validity of the Authentication, Authorization and Accounting (AAA) session for users? (Choose two.)
A Citrix Architect needs to evaluate and define the architecture and operational processes required to implement and maintain the production environment. In which two phases of the Citrix Methodology will the architect define this? (Choose two.)
A Citrix Architect has deployed NetScaler Management and Analytics System (NMAS) to monitor a high availability pair of NetScaler VPX devices.
The architect needs to deploy automated configuration backup to meet the following requirements:
The configuration backup file must be protected using a password.
The configuration backup must be performed each day at 8:00 AM GMT.
The configuration backup must also be performed if any changes are made in the ns.conf file.
Once the transfer is successful, auto-delete the configuration file from the NMAS.
Which SNMP trap will trigger the configuration file backup?
Scenario: Based on a discussion between a Citrix Architect and a team of Workspacelab members, the MPX Logical layout for Workspacelab has been created across three (3) sites.
The requirements captured during the design discussion held for a NetScaler design project are as follows:
Two (2) pairs of NetScaler MPX appliances deployed in the DMZ and internal network.
High Availability will be accessible for each NetScaler MPX
The external NetScaler MPX appliance will be deployed in multi-arm mode.
The internal NetScaler MPX will be deployed in single-arm mode wherein it will be connected to Cisco ACI Fabric.
All three (3) Workspacelab sites: Dc, NDR and DR, will have similar NetScaler configurations and design.
How many NetScaler MPX appliances should the architect deploy at each site to meet the design requirements above?
Scenario: A Citrix Architect has deployed Authentication for the SharePoint server through NetScaler. In order to ensure that users are able to edit or upload documents, the architect has configured persistent cookies on the NetScaler profile.
Which action should the architect take to ensure that cookies are shared between the browser and non-browser applications?

