A Citrix Engineer recently upgraded the environment from CVAD 2203 LTSR to CVAD 2402 LTSR and created multiple policy sets. How many policy sets can be assigned to a single Delivery Group?
Scenario: A Citrix ADC is configured with Interface 1/1 and bound to VLAN 40. A Citrix Administrator has executed the following command: bind vlan 20 –ifnum 1/1
What is the result of executing the command on the Citrix ADC?
Which qualifier is used to configure the Content filter action to modify the HTTP header of an HTTP Request?
Scenario: A Lead Citrix Administrator for a large company hired a new administrator for the team to help manage a Citrix Virtual Desktops infrastructure. The new administrator will need to manage user sessions and power-manage machines within the Delivery Group but should NOT be able to create any new objects.
Which role should the lead administrator create for the new administrator?
Scenario: A Citrix Administrator ran the Get-BrokerSite PowerShell command on the primary Delivery Controller to obtain overview information of the infrastructure.
The administrator received the error as shown in the exhibit.
Click on the Exhibit button to view the error.
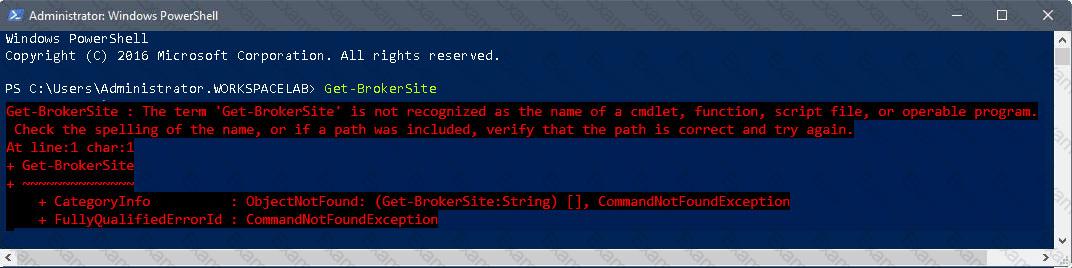
Why did the administrator receive this PowerShell error?
Scenario: The Director of network security in a financial organization wants to protect the enterprise network from any external malware threats. To do this, the director needs to gain visibility into otherwise-bypassed traffic and control access to malicious web sites. The director is required to do the following:
Intercept and examine all the traffic, including SSL/TLS (encrypted traffic), coming in, and going out of the enterprise network.
Block access to URLs identified as serving harmful or insecure content.
Identify users (employees) in the enterprise who are accessing malicious websites.
Which Citrix ADC deployment mode should a Citrix Administrator use to achieve this requirement?
Which Front-End Optimization (FEO) action can a Citrix Administrator use to achieve the results shown in the screenshots?
Click the Exhibit button to view the screenshots.
Scenario: A Citrix Administrator is implementing policies in a Citrix Virtual Apps and Desktops Site. The administrator is using both Active Directory Organizational Unit (OU) level GPOs and Citrix local-Site policies to maintain the Site. All non-Citrix user and computer policies are implemented through domain-level GPOs.
Which policies will be processes first for this Site when a user creates an HDX session?
Scenario: A Citrix Administrator configured Citrix ADC with multiple admin partitions, with different resources running one each. The administrator receives an SNMP alert stating ‘a Load Balanced Virtual Server is down’. When the administrator checks the Citrix ADC, the resource on the partition that was usually managed is NOT there.
Now, the administrator has to check each partition to find the load balanced virtual server that is down.
What can the administrator do to add the partition information to the SNMP traps to avoid this from happening in the future?
Scenario: A Citrix Administrator has a configured a Citrix policy using Citrix Studio. However, when the administrator restarted a Virtual Delivery Agent (VDA) machine and launched an HDX session hosted on that machine, the policy settings were NOT being applied.
Which three statements are possible reasons for this behavior? (Choose three.)

