As a valid Mobile Access Method, what feature provides Capsule Connect/VPN?
SmartEvent does NOT use which of the following procedures to identify events:
Using ClusterXL, what statement is true about the Sticky Decision Function?
Which configuration file contains the structure of the Security Server showing the port numbers, corresponding protocol name, and status?
To accelerate the rate of connection establishment, SecureXL groups all connection that match a particular service and whose sole differentiating element is the source port. The type of grouping enables even the very first packets of a TCP handshake to be accelerated. The first packets of the first connection on the same service will be forwarded to the Firewall kernel which will then create a template of the connection. Which of the these is NOT a SecureXL template?
You are investigating issues with to gateway cluster members are not able to establish the first initial cluster synchronization. What service is used by the FWD daemon to do a Full Synchronization?
When an encrypted packet is decrypted, where does this happen?
Traffic from source 192.168.1.1 is going to www.google.com. The Application Control Blade on the gateway is inspecting the traffic. Assuming acceleration is enabled which path is handling the traffic?
Under which file is the proxy arp configuration stored?
Which Check Point daemon monitors the other daemons?
To add a file to the Threat Prevention Whitelist, what two items are needed?
What are the blades of Threat Prevention?
: 156
VPN Link Selection will perform the following when the primary VPN link goes down?
How would you deploy TE250X Check Point appliance just for email traffic and in-line mode without a Check Point Security Gateway?
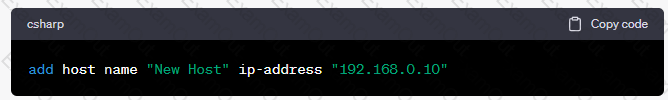
What API command below creates a new host with the name “New Host” and IP address of “192.168.0.10”?

 Firewall
Firewall Firewall
Firewall Firewall
Firewall