How many users can have read/write access in Gaia Operating System at one time?
How is communication between different Check Point components secured in R80? As with all questions, select the best answer.
Log query results can be exported to what file format?
Which Threat Prevention profile uses sanitization technology?
One of major features in R80.x SmartConsole is concurrent administration. Which of the following is NOT possible considering that AdminA, AdminB, and AdminC are editing the same Security Policy?
CPU-level of your Security gateway is peaking to 100% causing problems with traffic. You suspect that the problem might be the Threat Prevention settings.
The following Threat Prevention Profile has been created.
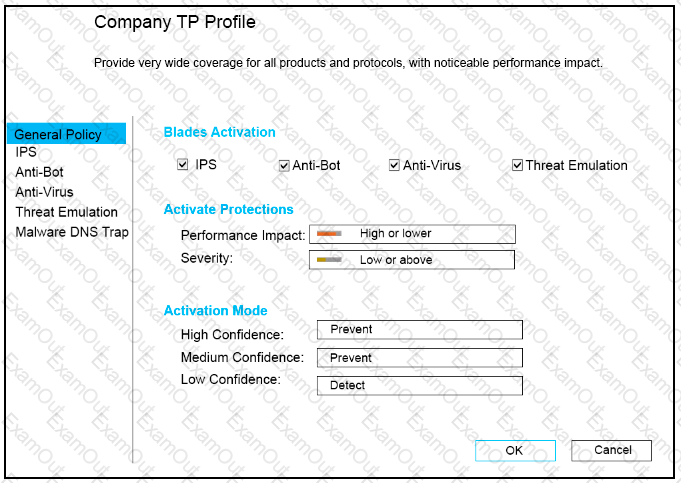
How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
Check Point licenses come in two forms. What are those forms?
In the Check Point three-tiered architecture, which of the following is NOT a function of the Security Management Server?
When connected to the Check Point R80 Management Server using the SmartConsole the first administrator to connect has a lock on:
Fill in the blanks: Gaia can be configured using the ____ or ____

