When an encrypted packet is decrypted, where does this happen?
What is the main objective when using Application Control?
Which Check Point software blade provides Application Security and identity control?
In SmartConsole, on which tab are Permissions and Administrators defined?
Consider the Global Properties following settings:
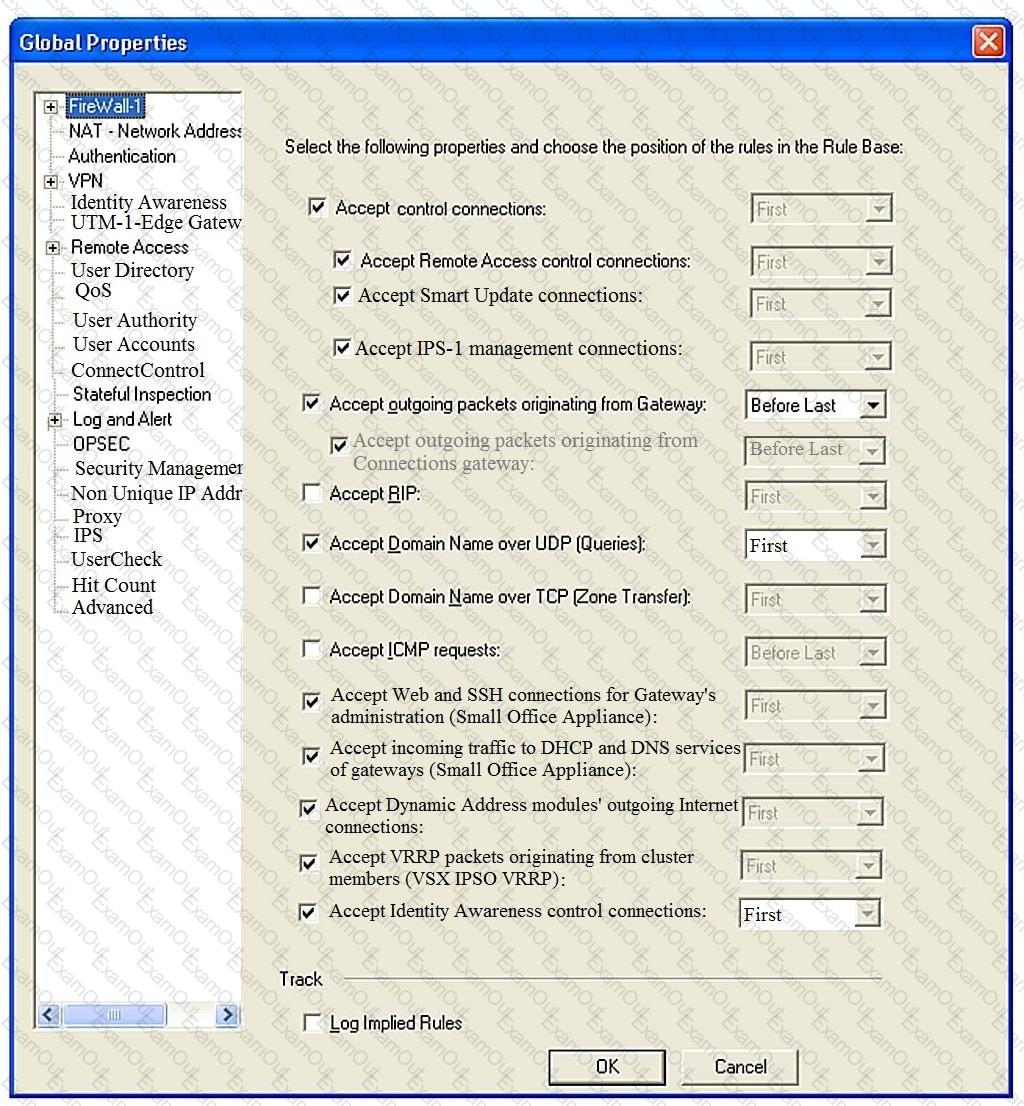
The selected option “Accept Domain Name over UDP (Queries)” means:
Name the utility that is used to block activities that appear to be suspicious.
When changes are made to a Rule base, it is important to _______________ to enforce changes.
True or False: In a Distributed Environment, a Central License can be installed via CLI on a Security Gateway
How Capsule Connect and Capsule Workspace differ?
Which of the following is NOT a tracking log option in R80.x?

