Which option would allow you to make a backup copy of the OS and Check Point configuration, without stopping Check Point processes?
In order to modify Security Policies, the administrator can use which of the following tools? (Choose the best answer.)
Using ClusterXL, what statement is true about the Sticky Decision Function?
Which statement is TRUE of anti-spoofing?
Which Security Blade needs to be enabled in order to sanitize and remove potentially malicious content from files, before those files enter the network?
At what point is the Internal Certificate Authority (ICA) created?
To quickly review when Threat Prevention signatures were last updated, which Threat Tool would an administrator use?
If the Active Security Management Server fails or if it becomes necessary to change the Active to Standby, the following steps must be taken to prevent data loss. Providing the Active Security Management Server is responsible, which of these steps should NOT be performed:
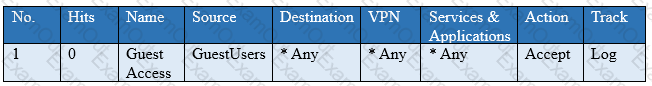
You have created a rule at the top of your Rule Base to permit Guest Wireless access to the Internet. However, when guest users attempt to reach the Internet, they are not seeing the splash page to accept your Terms of Service, and cannot access the Internet. How can you fix this?
What is true about the IPS-Blade?

