In a two-hour uninterrupted test session, performed as part of an iteration on an Agile project, a heuristic checklist was used to help the tester focus on some specific usability issues of a web application.
The unscripted tests produced by the tester's experience during such session belong to which one of the following testing quadrants?
A financial institution is to implement a system that calculates the interest rates paid on investment accounts based on the sum invested.
You are responsible for testing the system and decide to use equivalence partitioning and boundary value analysis to design test cases. The requirements describe the following expectations:
Investment range| Interest rate
R500 to RIO 00010%
RIO 001 to R50 00011%
R50 001 to RlOOOOO12%
RIOOOOl to R500 000| 13%
What is the minimum number of test cases required to cover all valid equivalence partitions for calculating the interest?
Which ONE of the following options is aPRODUCT riskand NOT aPROJECT risk?
Which of the following statements about the value of maintaining traceability between the test basis and test work products is not true?
Which ONE of the following options BEST describes Behavior-Driven Development (BDD)?
Which of the following is a task the Author is responsible for, as part of a typical formal review?
For each of the test cases to be executed, the following table specifies the priority order and dependencies on other test cases
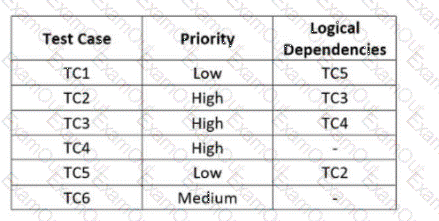
Which of the following test execution schedules is compatible with the logical dependencies and allows executing the test cases in priority order?
A software company decides to invest in reviews of various types. The thought process they have is that each artifact needs to be reviewed using only one of the review methods depending on the criticality of the artifact.
A company runs a pilot project for evaluation of a test automation tool. Which of the following is NOT a valid object of this pilot project?
An alphanumeric password must be between 4 and 7 characters long and must contain at least one numeric character, one capital (uppercase) letter and one lowercase letter of the alphabet.
Which one of the following sets of test cases represents the correct outcome of a two-value boundary value analysis applied to the password length? (Note: test cases are separated by a semicolon)

