A Systems Administrator is responsible for maintaining custom, approved AMIs for a company. These AMIs must be shared with each of the company’s AWS accounts.
How can the Administrator address this issue?
An Applications team has successfully deployed an AWS CloudFormation stack consisting of 30 t2-medium Amazon EC2 instances in the us-west-2 Region. When using the same template to launch a stack in us-east-2, the launch failed and rolled back after launching only 10 EC2 instances.
What is a possible cause of this failure?
The Chief Financial Officer (CFO) of an organization has seen a spike in Amazon S3 storage costs over the last few months A sysops administrator suspects that these costs are related to storage for older versions of S3 objects from one of its S3 buckets
What can the administrator do to confirm this suspicion1?
A company wants to create a new Network Load Balancer (NLB) (or an existing interface VPC endpoint. A SysOps administrator tries to remove the existing NLB but sees the error "existing VPC Endpoint connections and cannot be removed."
Which solution will resolve this issue?
A SysOps Administrator observes a large number of rogue HTTP requests on an Application Load Balancer (ALB). The requests originate from various IP addresses.
Which action should be taken to block this traffic?
A SysOps Administrator is troubleshooting Amazon EC2 connectivity issues to the internet. The EC2 instance is in a private subnet. Below is the route table that is applied to the subnet of the EC2 instance.
Destination – 10.2.0.0/16
Target – local
Status – Active
Propagated – No
Destination – 0.0.0.0/0
Target – nat-xxxxxxx
Status – Blackhole
Propagated – No
What has caused the connectivity issue?
A SySOps Administrator has created a new Amazon S3 bucket named mybucket for the Operations team. Members of the team are part of an IAM group to which the following IAM policy has been assigned.
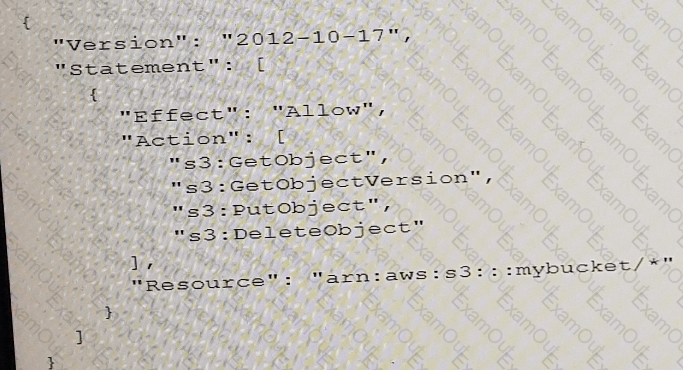
Which of the following actions will be allowed on the bucket? (Select TWO.)
A SysOps Administrator working on an Amazon EC2 instance has misconfigured the clock by one hour. The EC2 instance is sending data to Amazon CloudWatch through the CloudWatch agent. The timestamps on the logs are 45 minutes in the future.
What will be the result of this configuration?
An application runs on Amazon EC2 instances behind an Application Load Balancer (ALB). The instances run in an Auto Scaling group across multiple Availability Zones. The Information Security team wants to track application requests by the originating IP and the EC2 instance that processes the request.
Which of the following tools or services provides this information?
A Security and Compliance team is reviewing Amazon EC2 workloads for unapproved AMI usage.
Which action should a SysOps Administrator recommend?

